The landscape of IoT security: a tale of two futures

Anyone with a rudimentary knowledge of hacking can now specifically target IoT devices with little more than a click of a mouse.
Last month, while engineers around the world were building the next generation of connected devices, a piece of malware named Mirai was quietly going about its own business. While botnets — the colloquial term for a network of hacked devices working together — are always swirling around the internet, this one was different.Instead of targeting people’s computers or unprotected servers, Mirai was looking for a new type of prey. It was designed to scan the internet for any connected devices that use the telnet protocol – a system first developed in the 1960s but now dumped due to security concerns - and have factory-set passwords that no one thought to change.What did it find in its malicious net? Nearly 1.6 million internet-connected security cameras, DVRs and old web routers. Or devices we’d put under the banner, The Internet of Things (IoT). Once the malware had taken hold, it allowed the host to be used to direct huge volumes of web traffic to crash websites. In this case, it was the website of a known security journalist Brian Krebs and a hosting provider called OVH. In the former’s case, Krebs’ was bombarded with 78 GB of data every second, an unprecedented volume and double the size of the previous attack of this kind, according to security experts, Akamai.It’s no coincidence that Mirai, translated from Japanese, means ‘future.’ It’s a sign of things to come. Especially given that just a week after the attack, the malware’s source code was released to the general public. That means anyone with a rudimentary knowledge of hacking can now specifically target IoT devices with little more than a click of a mouse.
IoT is the hacking world’s new favorite toy
Mirai is not the only IoT specific piece of malware lurking on the web. Bashlight is another searching for shoddy security on these newly connected devices. According to research from security firm Level3 Communications, the Bashlight botnet has infected nearly four times as many devices as Mirai.But why is IoT so vulnerable to attack? Unfortunately, there’s a whole range of different reasons. One of the major issues is around out-of-date operating systems. When we read about botnets that are created on IoT devices, a lot of times those IoT devices are not suffering from a zero-day vulnerability, i.e a hacker finds a vulnerability before a fix for the device can be developed and released.Instead, the vast majority of compromises are due to IoT devices that have had a vulnerability that's been known about for months or years. Many are remotely deployed and some don’t even have traditional user interfaces, like screens and keyboards, making the process of upgrading them particularly troublesome.Another big issue around IoT security is down to the sheer variety of products inside the IoT ecosystem. To develop a patch for a known vulnerability and deploy it across a range of devices and ensuring that update worked is a mammoth task.Unfortunately, this issue is likely to get worse before it gets better. As the IoT ecosystem expands without a unified operating system - a standard way that items talk to each other – it makes creating security and secure communications across all of them a near impossible task.But there is hope, and it’s all about reducing the ‘attack surface’ of your products.
Here’s how to get ahead of hackers’ chess games
Take the Jeep Grand Cherokee. These cars are connected to a cellular network which open them up to an attack vector that a hacker can target. News broke the discovery of a vulnerability that allowed anyone to effectively break into the car and control it remotely. Even worse, once the vulnerability was discovered, there wasn't an effective procedure for installing updates to patch the hole remotely. The consequences of that vulnerability are too hellish to think about and it made Chrysler recall 1.4 million vehicles to patch the hole, by hand.
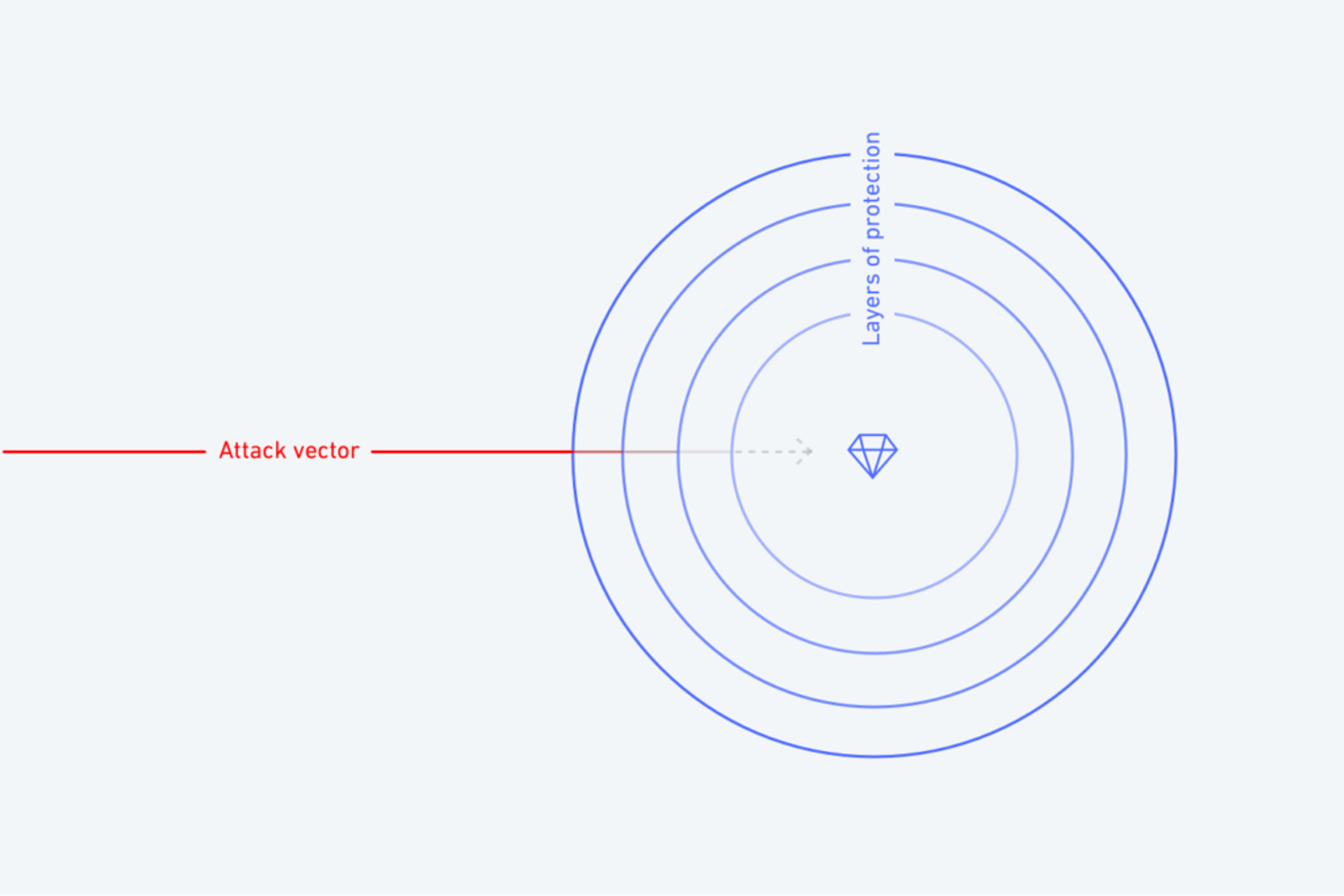
Hindsight is exactly that--hindsight--but here’s what we can learn from Jeep’s (tough) lesson learned as a case study:Think more holistically about security, exploring all avenues that hackers can take to gain vehicle accessImplement multiple security safeguards at various layers throughout the attack vector: Simply adding basic security at the network layer, for instance, would have disallowed attackers to gain access to the program controlling the vehicle despite vulnerabilities existing in other points along the attack vector.What’s important is that the developer community learn and grow, as IoT will soon touch on. There is no way that Jeep could have anticipated an attack of this magnitude, and no company is ill-intentioned.The bottom line is that developers should prepare for the worst.Here’s how Hologram’s CTO, Pat Wilbur, puts it:
“Consider this. Would it be foolish for a large banking institution to attempt to protect their most valuable assets by utilizing no passwords, no firewalls, no encryption, and wide-open wireless access points that enable any threat (inside or out) to see and access accounts and sensitive information in the clear? Of course! Now, if said bank addressed just one (only one) of these areas of insecurity, but ignored all of those other areas, would it be any less foolish?"The answer is that a holistic security policy should encompass several layers of security, from physical security, to application and transport, and to the network itself; clearly, this is no less true for wide-area and cloud deployments as it is for a local area network. Several security mechanisms should cooperate to achieve multiple layers of security, which eliminates the reliance upon any single mechanism for protecting against complete compromise of the system; when coupled with an ability to install updates frequently and in a timely manner, the probability of multiple mechanisms having known, unpatched vulnerabilities all at the same time approaches zero – and so does the chances of a system being successfully compromised by an attacker.”
In addition to considering best-practices like multiple layers of security, it’s essential for IoT developers to use well-known and well-tested technologies. The benefit there is that many eyes have looked over those applications. They've been around for a while. They're known to have been tested and for bugs to have been addressed.Another benefit is by using, as much as possible, off-the-shelf solutions for security. You benefit from a whole community of people who are maintaining that or depending upon updates, and then you're more likely to have an update if a vulnerability is discovered.Lastly, why invite burglars into your home for a cup of tea? Simple white-listing and firewalling can go a long way to supplement other security mechanisms and to thwart attack (although they should not be the only security constraints present).
The Future of IoT Security: a Tale of Two Stories
There are two versions of the future when it comes to security on the IoT. The first is to have stories like the Mirai and Bashlight becoming increasingly common and potentially scaring away the millions of people who could benefit from having IoT devices in their lives.The second, involves forethought--following the steps above to eliminate the guesswork from where the risks of an attack may lie.Since Mirai was unleashed, its ability to ensnare IoT devices has been steadily dropping as improvements to security have been made by manufacturers. Cisco has proclaimed that there will be 50 billion such devices by 2020, an eight-fold increase on what’s currently online today.It’s important for all of us that those 40 billion devices come prepared for the worst, otherwise it’s us that’ll suffer, not the machines.