Understanding cellular IoT security: Part 2

In part 2 of our 3-part blog series about understanding cellular IoT security, Hologram CTO Pat Wilbur discusses Software-Defined Networking and how it helps deliver a more robust security posture.
Part 2: What is Software-Defined Networking?
In Part 1 of this security series, I discussed that Hologram’s Software-Defined Network (SDN) provides advanced security out-of-the-box. In this blog, we’re going to review what SDN is and how it helps create a stronger security posture.
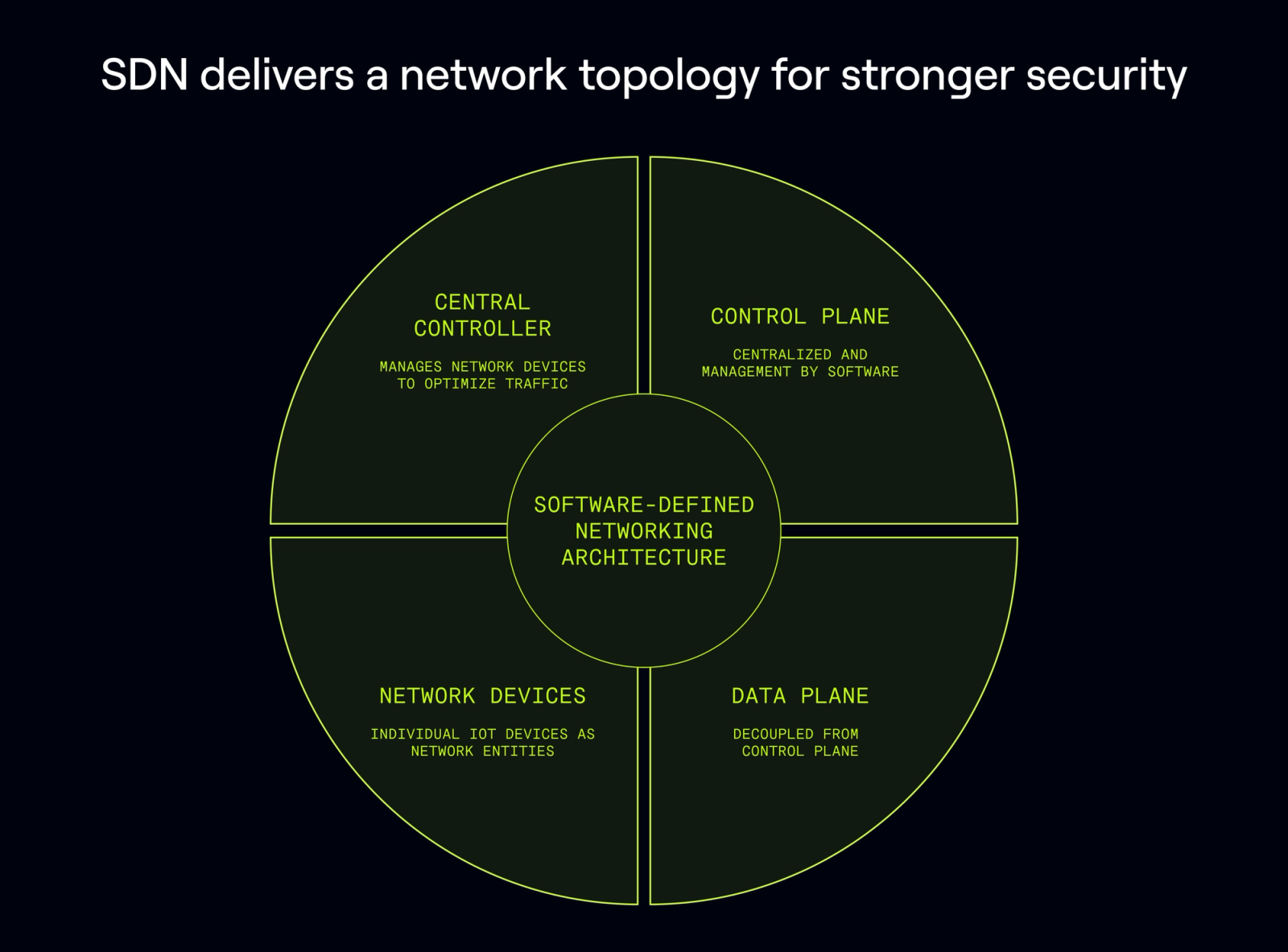
Software-Defined Networking (SDN) is a network architecture approach that allows for the centralized control and management of network resources through software. In the context of cellular IoT (Internet of Things), SDN is a powerful technology that can help optimize the performance, scalability, and security of IoT networks, which are increasingly complex and dynamic.
In traditional networking, network devices (routers, switches, etc.) often have both control (decision-making) and data plane (data forwarding) functionalities embedded in the hardware; and, where any logical separation between the two does exist, that separation is rigid and doesn’t scale beyond just a handful of logical segments.
With SDN, more granularity is possible, so the control plane is decoupled from the data plane and even individual hosts on the network (e.g. individual IoT devices) can be decoupled from one another. The control plane is centralized and managed by software, while the data plane is still distributed across the network hardware. The central controller communicates with network devices to configure and optimize network traffic.
Customizable security made easy
Decoupling means that you can apply different policies to different segments. That’s very powerful when it comes to security.
- Prior to SDN, rigid network functions (e.g. VLANs) could implement a small number of manually-configured network segments to logically separate devices; then, certain inter-segment routing/firewall policies could be applied at the border of each of the small number of segments, but all hosts within a particular network segment could communicate with any other intra-segment host.
- Now with SDN, you can create more segments and even isolate individual hosts/devices from one another. The end result is a better network topology for stronger security.
If you have one network that’s NOT purpose built for each device connection, but have to support a heterogeneous mixture of different devices and use cases, then you need to build your security policy to the common denominator, or union of the needs of every host/device.
Sure, sometimes this is fine. But, let’s go back to our Trust Services Criteria and the principle of reducing the attack surface. Often when trying to reduce the attack surface, it is better to logically group devices with similar characteristics and requirements. You can then create a purpose-built virtual network that satisfies just those requirements of a group of devices - like one with stronger controls to reduce the attack vector.
Why is this important today?
Back in the day, you might have a few computers in a network that all have similar security requirements. Now, one office building has a long list of devices and network access points - lighting and heating systems, air quality monitoring, security, computers, printers, mobile devices, and more. Each of those device categories may need different levels of security. With SDN, we can build a network specific to certain devices and apply security policies for a category of devices.
How Software-Defined Networking from Hologram delivers trust
Hologram’s Software-Defined Network (SDN) provides advanced security out-of-the-box today and can be adapted to meet your organization’s unique needs to grow with you tomorrow.
Here are three main areas where we leverage our SDN and criteria from the TSC to deliver trust.
Security
Hologram helps protect from unauthorized access and use.
Devices are isolated from the internet and each other.
We use a combination of network segmentation and multiple layers of firewalls to shield systems and devices from unauthorized traffic.
All traffic is authenticated and controlled.
Only authorized cellular devices can connect to Hologram's network. Controls such as data limits are enforced for each line of service. All inbound connections to devices are also authenticated.
Privacy
Hologram helps safeguard customer and device data.
Hologram has zero access to device data.
End-to-end encryption results in zero access by Hologram and its partners to customer / end-customer device data transmitted via cellular connectivity.
Our systems are compliant.
Customers use our connectivity in HIPAA and PCI compliant products. We conform to strict quality control and data security standards, such as GSMA SAS.
Trust
Hologram empowers innovators everywhere.
Hologram products have world-class quality.
Our SIMs are manufactured according to robust standards for the quality of products, material, integrity, strength, calibration, and environmental protection.
Hologram is global.
Our products and services are compliant with international regulations like GDPR. Our SIMs can be used in more than 190 countries.
As you explore cellular IoT providers, be sure to ask your cellular IoT provider how they are ensuring the security and confidentiality for your devices and data.
Keep learning about cellular IoT security in Part 3: Achieving your security goals. (Did you miss Part 1: Security Overview - The Trust Services Criteria?)