Access Point Names: What is an APN?

An Access Point Name (or APN), is a gateway between a cellular network and the internet. Here we explain how it works and more.
The APN is an important doorway between IoT devices and the network. It defines the type of connectivity and service a device receives, along with any individual settings. In this post, we’ll unpack the APN and take a closer look at its structure and format.
Click the links below to jump to what you need:
What is an Access Point Name (APN)?
What is an example of an APN structure?
What's the difference between an APN and a VPN?
Do I need a private APN for my IoT deployment?
What are the alternatives to a traditional private APN?
How can I resolve APN-related challenges?
What are the challenges with incorrect Access Point Name settings?
What is an Access Point Name (APN)?
APN stands for “access point name.” The APN provides a connection point between a cellular network and the internet, and can also help separate traffic from other networks. It’s an important entry point for cellular IoT devices because it defines the type of network access the device will receive and allows security.
Just as you can have multiple service set identifiers (SSIDs) on the same router or wifi access point, you can have several APNs on the same cellular tower, each with its own security settings and controls.
You can set one or more APNs on a single IoT device — and you must be connected to one in order to get any network resources, receive an IP address, or pass data over the network. You also have the option of connecting to multiple APNs at once with a single device.
The network can see the data that a device sends over an APN, and it applies rules on how to treat that traffic on the network. For example, a particular APN might have certain settings regarding firewalls, M2M data routing, or which gateway is used to link to the internet. The path your data travels will depend on which APN you’re connected to and how it’s configured on the network side.
Ultimately, the APN serves as a doorway between your device and the wider network (either a private network or the internet) — a doorway with particular settings or security instructions attached to it.
How is an APN structured?
An APN follows a prescribed structure and identifies two main components: the network and the operator. The network identifier names the network, while the operator identifier names the MNO. Within the operator identifier are the Mobile Network Code (MNC) and the Mobile Country Code (MCC), each typically three digits long. At the end of the APN, there’s a suffix that identifies a particular data standard: either GPRS or 3GPP.
What is an example of an APN structure?
An example of an Access Point Name (APN) structure might appear as follows:
mobile.mnc001.mcc310.lte
- mobile: This segment represents the network identifier, indicating a connection to the mobile network.
- mnc001: The Numbering Code (MNC) specifies the network code for the mobile operator.
- mcc310: The Country Code (MCC) indicates the country, with 310 representing the United States.
- lte: This part shows that the connection standard used is LTE, a shared high-speed data transfer technology.
This format allows mobile devices to connect to and communicate with their chosen networks, ensuring smooth data transactions and consistent network access.
What's the difference between an APN and a VPN?
Understanding the fundamental roles of APNs and VPNs in network connectivity is essential for fully appreciating their nuances. Both play distinct yet crucial roles in how devices access and interact with networks.
Access Point Name (APN)
An Access Point Name, or APN, acts as a gateway, allowing devices to connect to the internet through a carrier network. It’s essentially the bridge that links your device to the broader web, determining how your device connects to the internet and what security measures are in place.
There are two basic flavors of APN: public and private. Each has advantages and variables associated with it, so let’s examine them more closely.
Public APN
Many mobile network operators (MNOs) offer users a public APN with basic configurations for connecting to the internet. It provides for typical tasks that devices do on the network, and many customers often share the same APN. The public APN might include security features such as firewalling access from outside internet devices, which prevents one device from talking to another if it’s not recognized in the network. Ultimately, the public APN gives you a simple, vanilla configuration that gets you access to the network, but it doesn’t let you customize settings and security features you might need for an IoT deployment. If the APN is defined as a public APN with static public IP, it will assign an IP address to a device that will become that device’s distinctive IP, used every time it connects to the network.
Private APN
A private APN allows you to drill down and customize network settings. With it, you can build a network that’s tailored to your needs. In the past, you’d have to roll out extensive infrastructure to achieve a truly private APN. Today, attaining the same level of network personalization is becoming simpler. If you’re on an APN backed by a software-defined network (SDN), you can essentially build your own virtual mobile network without the added expense of creating physical infrastructure.
Virtual Private Network (VPN)
In comparison, a Virtual Private Network, or VPN, is a technology that creates a secure connection to another network over the Internet. It extends a private network across a public network, allowing you to share data across the public network as if you’re connected to a private network. In essence, it’s a tunnel that will enable one private network to connect to another via the public internet – while maintaining the security and privacy of both private networks. The VPN encrypts and authenticates all traffic traveling through the tunnel to achieve that.
Understanding these differences clarifies how each technology can be applied to meet specific connectivity needs, whether you're prioritizing security, customization, or basic internet access.
How do APNs and VPNs fundamentally differ in their purpose?
APNs primarily connect devices to the Internet through a carrier network. In contrast, VPNs are designed to create secure, private connections between networks over the Internet, protecting data in transit.
What is a VPN?
A Virtual Private Network (VPN) is a technology that establishes a secure, encrypted connection to another network over the Internet. It ensures privacy and protection for data transferred across networks.
What is an APN?
An Access Point Name (APN) is a gateway that lets you connect to the Internet via your mobile carrier's network. It facilitates the connection between your device and the wider web.
Do I need a private APN for my IoT deployment?
Depending on your use case, you might not need a private APN for your IoT deployment. But because a private APN (or another option that can offer the same functions) gives you the power to implement your own firewall rules and security settings instead of using defaults, it offers many useful tools. For example, if you’re launching a product and want to reduce your attack surface, a private APN can help protect your devices by keeping them off the public internet.
Some other advantages of choosing a private APN include the ability to customize your IP address space, restrict inbound access to devices behind a firewall with a virtual private network (VPN), and route traffic through a VPN tunnel. You can also use a private APN for outbound firewalling if you need to restrict the destinations your devices can connect to, or to create a second layer of data encryption.
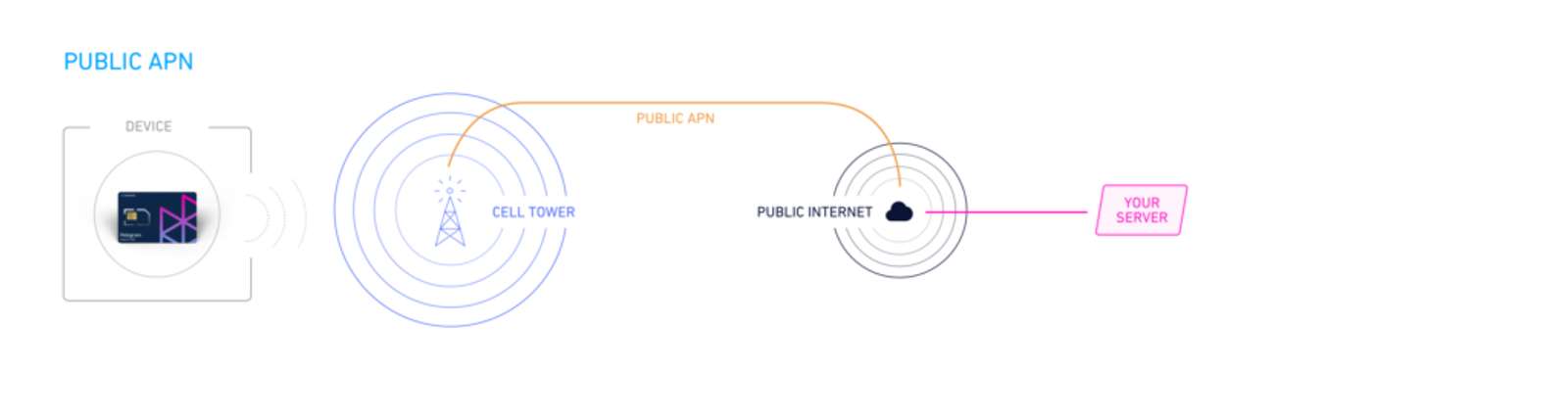
Wait, what is a VPN?
A virtual private network (VPN) extends a private network across a public network, allowing you to share data across the public network as if you’re connected to a private network. In essence, it’s a tunnel that allows one private network to connect to another via the public internet — while maintaining the security and privacy of both private networks. To achieve that, the VPN encrypts and authenticates all traffic traveling through the tunnel.
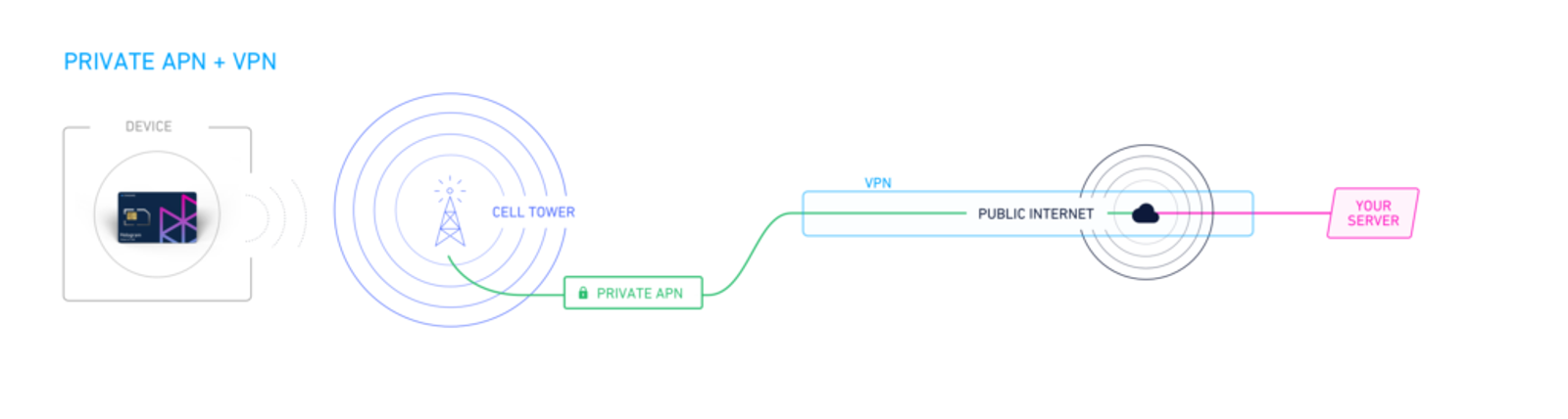
Companies that establish a private APN often get a VPN link to connect their private APN with the company’s own private network, whether it’s on-premise or in the cloud. If you use a VPN to connect your company’s private networks, you can draw a big circle around those networks and call that your wide-area network (WAN). Mobile devices on the WAN are still isolated from other mobile devices on other APNs. Even though the VPN tunnel might traverse the public internet or another public network, it’s still maintaining privacy, giving you the same benefits as an internal private network.
What are the alternatives to a traditional private APN?
Private APNs offer enhanced configurability, device security, and data privacy. But they can be expensive to establish — often requiring the build-out of additional network infrastructure that you might not have planned on creating. The good news is, thanks to recent innovations around software-defined networks (SDNs), there are other options that can deliver the same privacy and WAN capabilities without a private APN. Let’s take a look at a few of those alternatives.
Shared private APN
In one sense, a shared private APN is similar to a public APN because you don’t need to spin off additional APNs — but it’s backed by a customizable and secure SDN. It’s a network that allows you to create additional virtual segments and apply different policies and settings as needed. Choosing a shared private APN can decrease your time to market, upfront costs, and self-service access — rather than having network engineers build a network for you, you can manage your own WAN and do a lot of your own customizations. If you know what your end goal is and how to make those adjustments, it’s an advantage to be able to have access and configure it yourself. And since this option is software-defined (rather than configured on physical infrastructure), your network can evolve along with your business.
Cloud-to-device messaging
Some use cases require a persistent or session-based connection, and for that they need a VPN tunnel or a solution like Spacebridge that allows for constant connections to be tunneled into the network. But what about use cases where devices are not constantly connected? For example, you don't need a persistent network connection if you want to unlock a gate, open a garage door, or send a command to a device to perform an action. To accommodate these IoT use cases, Hologram also offers an API for sending short commands. Traditionally, a VPN or similar solutions would require you to have a private network, or build a virtual one, to set up this virtual networking infrastructure — but Hologram’s cloud-to-device messaging function doesn’t require you to maintain any of these tunnels. All you need is a device ID and a message, and it will be delivered to the device. Depending on your application, this option can reduce costs and enable scalability.
Application-layer solutions
In some cases, application-layer solutions will make fine alternatives to establishing a private APN. For example, the MQTT protocol is an alternative to cloud-device messaging — and you don’t need to set up anything to use it if your device already has it or a similar burst protocol configured. Another workaround is the device-based VPN or WAN solution, where the device connects to your network over a VPN or similar protocol. Implementing security at the application layer is always a best practice, but be sure to weigh the pros and cons of each addition. Application-layer solutions tend to add complexity, making it more difficult to push a new solution down to the endpoints (because the devices may not support it).
Are you struggling with APN-related issues on your device? Here’s a few troubleshooting tips to help you.
Verify your APN settings
- Check your carrier’s information: The first step is to ensure your Access Point Name (APN) settings are correct. Visit your carrier or MVNO’s website or contact their support to obtain the correct details.
- Spot the errors: Review your current APN settings and cross-check them with the information from your carrier or MVNO. A small mistake, such as a misplaced letter or digit, can cause connectivity problems.
Reset to default settings
- Utilize built-in options: Many devices can reset APN settings to default. This feature can quickly fix discrepancies if the accurate settings aren't easily available.
- Note of caution: If you’re using a custom APN, make sure to jot down your settings before resetting, as this action might erase them.
Manually input the APN details
- Input with precision: If the automatic correction doesn’t work, manually input the correct APN details. Make sure you fill in every field precisely according to what your carrier or MVNO provides.
- Thorough check: Before saving the changes, carefully review the input to ensure it matches.
Reach out to your carrier
- Seek expert assistance: Contact your carrier’s technical support if you still have issues. They can provide device-specific solutions or additional troubleshooting.
- Investigate account concerns: Sometimes, the problem might be on your carrier or MVNO's end due to account configuration issues. Only their support team can address these.
By following these steps, you can effectively tackle APN-related problems and achieve uninterrupted connectivity.
What are the trade-offs?
If you’re deliberating between building a traditional private APN and choosing an alternative, there aren’t many trade-offs these days. If your provider only offers a private APN option, that may be the only path available to you — but if you’re working with Hologram or another provider that supports software-defined network solutions, you have simpler, faster, less costly options that offer all the same benefits of a private APN without the need to construct your own network.
What are the challenges with incorrect Access Point Name settings?
When Access Point Name (APN) settings go awry, multiple issues can arise that affect your device's connectivity and functionality.
Connectivity complications
- Lack of data connection: This is the most common issue. Incorrect APN settings can prevent your device from connecting to your mobile network, shutting you off from the internet and any data-reliant apps.
- Unstable connections: Even if there is connectivity, instability can often follow. This might manifest as frequent disconnections or sluggish data speeds, disrupting your device performance and end-user experience.
Service limitations
- Multimedia Messaging System (MMS) hiccups: APN settings are critical for sending and receiving MMS messages. Incorrect configurations can impact this process, stopping the flow of pictures and videos.
- Tethering troubles: Faulty APN settings can make using your phone as a hotspot problematic. Other devices may struggle to access the internet through your mobile data.
- Exclusive carrier services: Some network providers offer unique services, such as proprietary applications, which depend heavily on proper APN settings for functionality.
Financial impacts
- Loss of revenue: Revenue-generating devices, like mobile POS, simply won’t connect if the device uses the wrong APN which can result in significant financial losses.
- Eroded customer confidence: Customers expect connectivity to work flawlessly. Failing to meet end-user expectations results in lost customers and lost trust in the brand.
Troubleshooting challenges
- Identifying the problem: Identifying APN settings as the root cause of connectivity issues can be tricky. These settings often go overlooked during initial troubleshooting efforts.
- Check for typos: The impact of incorrectly set APNs can vary. A minor error, like a typo, might lead to minor inconveniences, whereas a completely incorrect APN can block data usage entirely.
Hologram makes it easy
Hologram SIMs are hardware-agnostic and should work with any hardware that is not locked to a carrier. Simply configure your device to use Hologram’s Access Point Name (APN). This allows your device to properly set up a connection to the gateway between Hologram and the Internet. With Hologram, you can help ensure your devices have the connectivity, coverage, and reliability you need.
Recommended Reading: What are IMEI and TAC numbers & Why do they matter?
Recommended Reading: How multi-IMSI and cellular IoT work together